Facts About It Service Melbourne Uncovered
Wiki Article
More About It Service Melbourne
Table of ContentsThe 30-Second Trick For It Service MelbourneThe Only Guide to Managed It Services For Law FirmsHow Managed It Services Melbourne can Save You Time, Stress, and Money.About It Services Melbourne
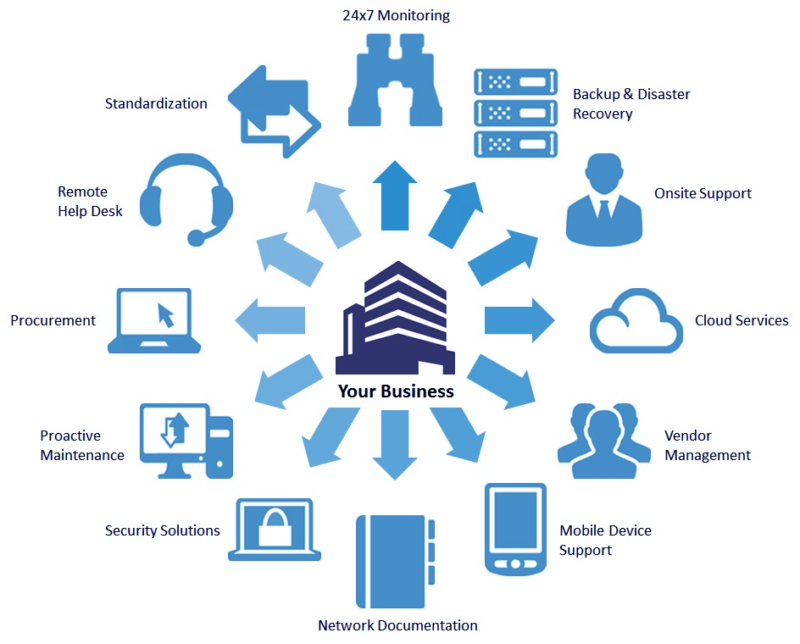
As foresaid, IT support deals end-to-end handled IT solutions, which include these mostly: An IT infrastructure has a variety of laptop computers, workstations, printers, web servers and hardware systems. A little damage or malfunction might end up in a wonderful loss, which can be of vital data or info. This occurring eventually effect on the company's returns as well as continuity.This is remarkably for the business that enable workers to use their very own phones for performing jobs. The assistance offering business position their group to protect that data and possessions from hackers or abuse.
It makes certain that just secure tools will certainly have the ability to do from another location, as they would certainly can safeguarding the delicate information of the business. It refers to the on-demand schedule of computer system resources, including data storage space and computing power. This happening does not call for any kind of direct energetic monitoring by the user.
As its advantages are outstanding, an increasing number of business have begun shifting to the cloud for organizing their data. managed it services for law firms. For maintaining their secret information regarding customers as well as their consumer experience (CX) secure, it includes some exceptional protection features. The tech support team handles it well in 2 methods: Making certain configuring as well as handling the cloud system for organizing a number of requisite applications, information management, IT support and also downtime, Supplying the total security to what comes under the managed IT solutions from cyber lawbreakers.
Not known Facts About Managed It Services Melbourne

Something went wrong. Wait a minute as well as try again Attempt once more.
Services are increasingly relocating their IT infrastructures right into the cloud. Many business companies now operate in multi-cloud settings or use hybrid on-premises and cloud-based IT architectures.
The Single Strategy To Use For Managed It Services
Involves testing information healing remedies to guarantee that they are trusted and efficient in the occasion of a data loss or corruption. IT sustain is essential for services that count heavily on their data, such as those in the health care and finance industries.Work environment technology alters swiftly as well as gets more complex by the year. Whereas the bulk of job-related computer once occurred within the office walls and inside a safe and secure border, today's dispersed labor force conducts organization from homes, coffee bar, autos literally anywhere with net access. Sustaining as well as protecting the myriad gadgets as well as accessibility points employees currently rely upon to remain effective has developed a whole lot even more job for IT groups that usually are currently spread out as well slim.
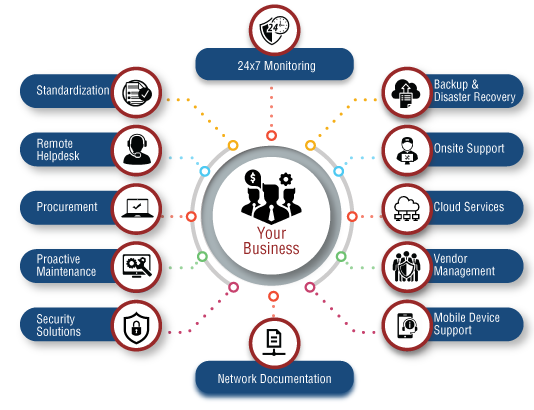
Organizations count on taken care of companies (MSPs) for a range of factors, but the majority managed it services for law firms of generally, they are used by organizations without any inner IT team or those that wish to utilize their internal IT experts to concentrate on certain campaigns as opposed to operational obligations for managing technology. MSPs give a vast variety of services from the basics such as assistance workdesk support and keeping IT tools as well as services functioning completely as much as providing the full collection of IT capacities, including cyber safety and security, net connection, application assistance, information back-ups, and also disaster recuperation.
It Services Melbourne for Dummies
Handled IT solutions are far from one-size-fits-all, so partnering with an MSP that recognizes your organization and also is proactively bought assisting you satisfy your objectives is important.Potential threats outside the network are prevented, guaranteeing that an organization's sensitive data remains inside. Organizations can go further by specifying added internal limits within their network, which can offer enhanced safety and security and also accessibility control. Access control specifies individuals or teams and also the tools that have access to network applications as well as systems thereby refuting unsanctioned accessibility, as well as possibly dangers.
A vulnerability is a fancy circumstances in a software system and a manipulate is an assault that leverages that vulnerability to get control of that system. When an exploit is introduced, there is commonly a window of chance for attackers to manipulate that vulnerability prior to the safety and security patch is used.
Sandboxing is a cybersecurity technique where you run code or open files in a safe, separated environment on a host equipment that imitates end-user operating atmospheres. Sandboxing observes the documents or code as they are opened and searches for malicious actions to stop hazards from hopping on the network. As an example malware in data such as PDF, Microsoft Word, Excel and also Power, Point can be securely found as well as obstructed prior to the documents reach an innocent end individual.
Report this wiki page